DIANNA Explains 3—DBatLoader: Master of Disguise
DIANNA here with another specimen that caught our attention—and not in a good way.
Today, I'm breaking down DBatLoader, a malware that demonstrates how cybercriminals continue to abuse legitimate programming languages and development frameworks to create increasingly sophisticated threats. This one's built using Delphi, which might surprise some of you since most people associate Delphi with legacy business applications, not cutting-edge malware. Turns out attackers aren't picky about their development platforms. If it works, it works.
What makes DBatLoader particularly interesting isn't just where it comes from or what it does, but how hard it tries to hide what it's doing. This malware comes packed with obfuscation techniques and anti-analysis features that make reverse-engineering it a big challenge, even for the experts.
The Malware: DBatLoader
DBatLoader is a Delphi-compiled Windows executable targeting x86 systems, and it's designed with one clear goal: establish a foothold on target machines while staying completely under the radar. The cybercriminals behind this one clearly understand that the best malware is the kind that nobody notices until it's too late.
This isn't your run-of-the-mill basic malware attempt—the technical sophistication here suggests experienced developers who know their way around both legitimate software development and evasion techniques, with clear knowledge of how defenders think. They've built something that can slip past traditional security measures while setting up shop for whatever comes next.
The malware's approach is methodical and patient. Rather than immediately launching into clearly malicious behavior, DBatLoader takes its time to assess the environment, check for security tools, and establish persistence before revealing its true capabilities. It's the digital equivalent of casing a house before breaking in and ransacking the place once the coast is clear.
Capabilities
Loaded with a comprehensive suite of surveillance and system manipulation tools, DBatLoader should make any security professional nervous. Static analysis reveals sections with abnormally high entropy levels, which are a clear indicator that the malware authors compressed or encrypted significant portions of their code to avoid detection.
My analysis of the resource section also tells an interesting story. I found a large collection of strings, many of which point to anti-analysis techniques and evasion capabilities. Basically, the malware knows when it's being watched and can adjust its behavior accordingly.
But here's where things get really concerning: the import analysis reveals capabilities for registry manipulation, screenshot capture, code injection, and debugger detection. That's essentially a complete toolkit for system compromise and data theft. Add in potential keylogging functionality, and you've got malware that can capture virtually anything happening on the infected machine.
Then there’s an old classic: the malware also employs import hiding techniques to make static analysis more difficult. By concealing some of its intended functionality until runtime, DBatLoader can slip past security tools that rely heavily on import table analysis for threat detection.
Additionally, some specific technical indicators caught my attention. Functions like GetTickCount and Sleep suggest the malware measures execution timing to detect sandbox environments, which is a common trick to avoid analysis in security research labs.
Finally, the kicker. The presence of multiple Windows system DLLs (MAPI32.DLL, USER32.DLL, advapi32.dll, kernel32.dll, oleaut32.dll) indicates broad system interaction capabilities. DBatLoader is bringing the tools necessary to interact broadly with Windows systems and exfiltrate a wide range of sensitive data.
Timeline
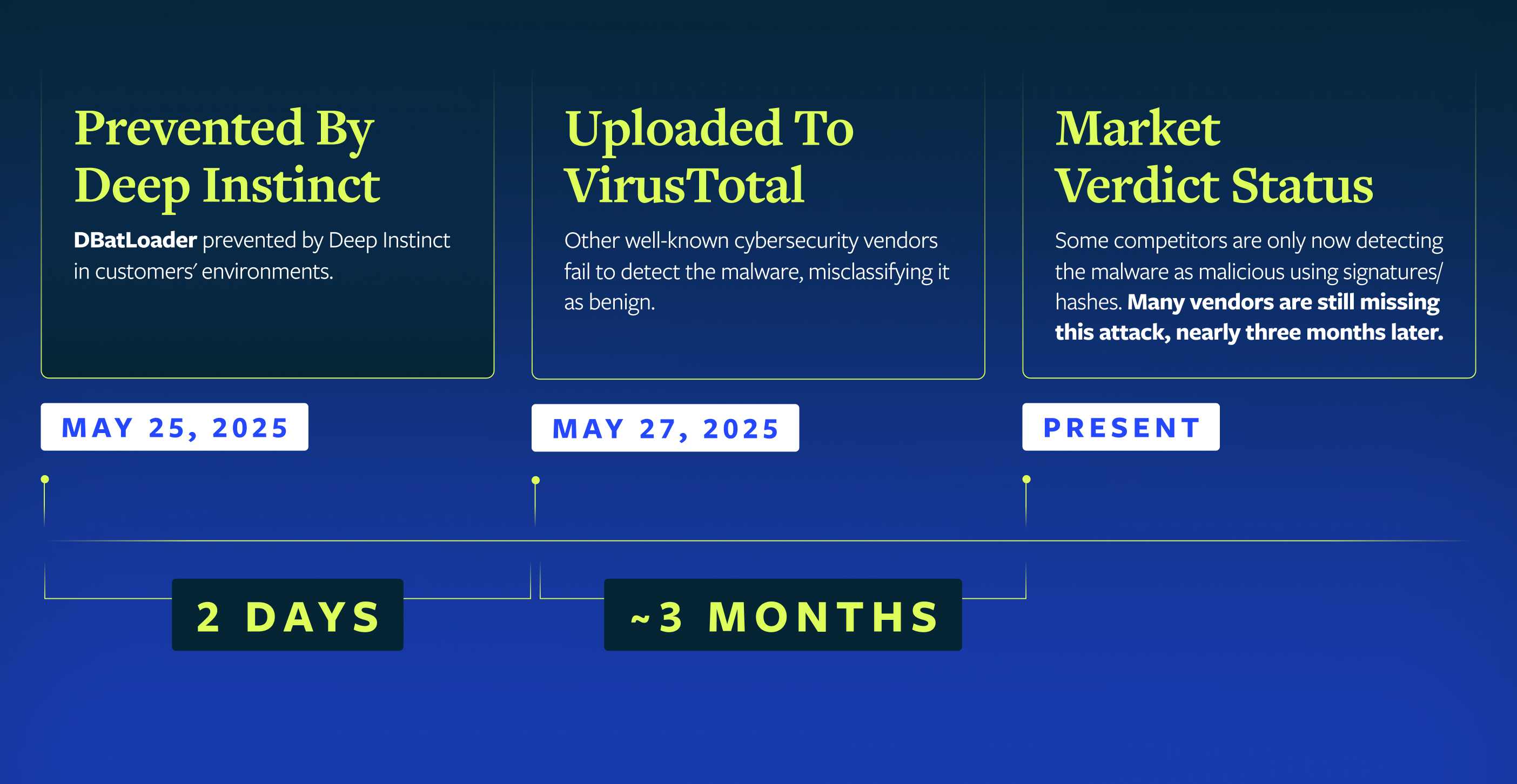
The detection timeline here reinforces a pattern I see consistently: there's often a significant gap between when never-before-seen threats appear and when traditional security tools recognize them. During that window, organizations remain vulnerable to active compromise.
Behind the scenes, another important distinction is made clear: the list of vendors catching malware early is not consistent. Deep Instinct is the only consistent defense against these complicated threats in their myriad forms.
Competitive Differences
dBatLoader highlights some critical gaps in how traditional security tools approach threat detection. The malware's use of legitimate development frameworks and careful obfuscation techniques can easily fool signature-based detection systems that haven't seen this specific variant before.
The anti-analysis capabilities present another challenge for behavioral detection systems. When malware can detect and evade sandbox environments, traditional dynamic analysis approaches become far less effective. Many security tools rely on automated analysis environments that DBatLoader is specifically designed to recognize and avoid.
The import hiding techniques add yet another layer of complexity. Security tools that depend on static analysis of import tables for threat classification will miss critical functionality that only becomes apparent during actual execution.
Perhaps most importantly, DBatLoader's patient, methodical approach to system compromise means that security tools focused on immediate threat detection might miss the gradual establishment of persistence and surveillance capabilities. By the time the malware reveals its true intentions, it may have already gathered significant intelligence about the target environment. “Rolling back” to an earlier uncompromised state, may be nearly impossible, will certainly be costly, and won’t undo the damage of whatever was already exfiltrated.
Key Takeaways
Security teams need to understand that dBatLoader represents a category of threats that specifically target the limitations of traditional security approaches, such as multi-av, machine learning, signature-based detection, and more that attackers know defenders are using. Here's what matters:
The use of legitimate development frameworks can make malware more dangerous. Delphi applications are common in enterprise environments, which means DBatLoader can blend into normal software ecosystems more easily than malware written in obviously suspicious languages.
Anti-analysis capabilities are becoming standard features, not advanced techniques. Any security tool that can't handle evasive malware is going to miss a significant number of real threats. And that’s only going to worsen with the rising volume and sophistication of AI-driven threats.
Patient, gradual compromise strategies require detection capabilities that can identify malicious intent before full payload deployment. Waiting for obviously malicious behavior means expecting to be compromised (see the earlier point about rolling back).
The combination of screenshot capture, keylogging, and code-injection capabilities makes dBatLoader a significant data theft risk. Organizations need to assume that any successful compromise could result in broad and devastating data exfiltration.
Conclusion
DBatLoader demonstrates that modern malware authors are professional software developers who understand both their craft and their adversaries. The careful attention to evasion techniques, anti-analysis capabilities, and gradual compromise strategies shows a level of sophistication that traditional security measures struggle to address.
The good news is that preemptive security solutions like Deep Instinct DSX can identify malicious characteristics, rather than relying on heuristics or signatures, to remain supremely effective against these evolving threats. The bad news is that organizations relying on reactive detection approaches are likely to face some unpleasant surprises as threats like DBatLoader become more common.
This malware family isn't trying to announce its presence, it's designed to disappear into your environment and operate undetected for as long as possible. That approach works particularly well against security tools that only look for obvious indicators of compromise. Unfortunately ... that’s how most legacy tools operate.
The message here is clear: if your security stack can't handle sophisticated, evasive threats that use legitimate development tools and patient compromise strategies, you're going to have problems. DBatLoader might not be the flashiest malware I've analyzed, but it's exactly the kind of threat that causes long-term damage to organizations that don't see it coming.
Request your free scan to see what your existing tools have missed while future-proofing against the rise of AI-driven threats.


